Investigating ethical crimes
Edward J.S. Morris and Catherine P. Zuluaga
RMIT University, Australia
ABSTRACT
To improve final year information technology (IT) undergraduate students' ability to analyse ethical issues, we devised a five-step procedure, based on a standard investigative procedure used at crime scenes. The appeal to our students lies in associating the investigation of an ethical issue with the investigation of a crime, as portrayed in popular television crime shows that add modern forensic science to traditional 'whodunnit' mysteries.
We evaluated the success of our ethical 'crime' investigation procedure by comparison with previous student cohorts given the same issues to analyse. To leverage the strengths of our new approach, we scripted an ethical crime scenario for video production. The video depicts events surrounding a petty theft in a busy open plan office. Students investigate first the crime, then the underlying ethical issues.
To help online students learn to investigate ethical issues, we used our previously reported object oriented learning methodology (OOL) to design a class of learning objects, or learning object class (LOC). Class Investigator uses our ethical crime investigation procedure and example video. This LOC facilitates dynamic instantiation of an individualised learning object (LO) for, or by, a student during a lesson. This enables a LO lesson to be not only more highly interactive but also far less predetermined in its sequence of activities for each student.
Keywords: Computer ethics; learning object; object-oriented; online; software engineering.
1 INTRODUCTION
Computer ethics is an integral part of the computing curricula formulated by the joint task force (ACM, AIS, IEEE-CS (Association for Computing, 2005) for tertiary degree students in computer science (CS), computer engineering (CE), software engineering (SE) and information systems (IS). However, during 10 years' experience teaching computer ethics, we concluded that many information technology (IT) students (CS, CE, SE and IS) have difficulty applying a standard procedure (Morris, Zuluaga, R., Zuluaga.C., 2004) for systematically analysing a (computer) ethical issue.
Fortunately, one addition that benefits students learning the finer points of computer ethics is analogical thinking (Johnson, 2001). For example, the cyberspace ethics methodology (Morris, 1999) proposes a step-by-step procedure for analysing a cyberspace ethical issue by analogy with an issue in 'real' space. As this methodology had some success engaging IT students in cyberspace ethical issues (e.g., virtual rape), we report here on our continuation of this analogical approach as follows.
We developed a procedure for analysing ethical issues that is based on a standard investigative procedure used at crime scenes. The appeal to our students lies in associating the investigation of an ethical issue with the investigation of a crime, as portrayed in popular television crime shows that add modern forensic science to traditional 'whodunnit' mysteries.
Section 2 describes the difficulties our students formerly exhibited when analysing an ethical issue. Section 3 explains our ethical 'crime' investigation procedure and reports a preliminary evaluation of its benefits. Section 4 outlines a video we produced to illustrate a crime with underlying ethical issues. We show how students are first asked to investigate the crime, then encouraged to investigate similarly one or more underlying ethical issues.
Our video is useful not only in a face-to-face class; it can also be embedded in a learning object (LO) for delivery online or via CD-ROM or television broadcast. These media will be utilised when the course is delivered 75% online in Africa and 50% online in Vietnam, Singapore and Malaysia. Section 5 outlines the design of our ethical crime LO.
2 IT STUDENT DIFFICULTIES WITH ETHICAL ISSUE
2.1 IT student profile
Our computer ethics course is taken mostly by final year IT students (CS and SE included). These students are highly IT literate. At the start of the course, they are well aware of what IT can do, but the majority are not familiar with ethical issues raised by IT. Initial feedback indicates these students are blasé or naïve about the 'dark side of the IT force'. We observe that they focus on technical issues and largely ignore ethical and even legal aspects.
Almost all our students acknowledge that IT users in general are vulnerable to the 'dark side' of IT. However, the prevailing attitude among our students at the start of the course is that users need to become better informed, rather than that IT professionals need to do more to safeguard public interests. We challenged this perception with some success during the professional ethics component of the course.
A minority of our students are knowledgeable about hackers, viruses, spyware, etc – but still mostly the technical aspects. Our impression is that these students think that they know enough to defend themselves against such attacks, so they did not need to delve further.
Few of our students feel disposed to explore IT ethical issues per se until they become aware of deeper aspects, which they were ill prepared to deal with, e.g., information privacy requirements in a network they might design, implement or administer. Our first job is to inform these budding professionals of their legal obligations and the underlying ethical considerations.
Once our students started showing enthusiasm to tackle IT ethical issues, it became clear that a significant cohort was not well prepared in terms of their educational backgrounds. Many of our students have a non- English speaking background (NESB). This can be a disadvantage when discussing or analysing ethical issues that generally involve complex vocabulary and grammar. Any legalities (or 'legalese') compound this disadvantage. And the average NESB student does not easily discern any use of subtlety or nuance in the English language.
An even larger deficit for most of our students is the lack of educational background in arts/humanities, e.g., literature, philosophy or history. Instead our students' extensive backgrounds in mathematics, sciences and engineering lead them to expect an ethical issue to be 'black and white' with a single solution.
In our experience the best way to assist our students to explore IT ethical issues is to provide structured problems, systematic procedures and analytic techniques wherever possible.
2.2 Basic procedure for analysing ethical issues
During the early years of our course, for the ethics component we asked our students to use the following procedure to analyse three IT ethical issues, each encapsulated in one of Johnson's scenarios (Johnson, 2001). This analysis procedure is loosely based on that of Kalliman and Grillo (1996), but we do not introduce the application of ethical theory until later in the course when we re-analyse the scenarios in greater depth.
For each ethical problem scenario, the initial analysis procedure is:
- Identify the players in the scenario and their interests; i.e., identify the parties and specify the facts.
- Explain the ethical problem faced by the players; i.e., define the moral dilemma.
- List alternative solutions to the defined problem; i.e., formulate the options.
- Clarify the principles at stake and their implications; i.e., highlight the values and their outcomes for the parties.
- State your solution to the ethical problem; i.e., prioritise the values and outcomes, then select the most appropriate option. Also give a short rationale for your solution.
Although each scenario is necessarily artificial, and its ethical issue or problem is far simpler to analyse than a real one, many of our students found each step increasingly difficult.
In step 1, some students included every named person as a player. This was rarely wrong in these simple scenarios because each person is intended to be instrumental to the ethical issue. But few students distinguished main players. We observed that students did not realise in a real ethical issue that not every person is a main player or a player at all.
In step 2, quite a few students seemed to assume that all players had their own personal ethical issue, or at least their own perspective on it. So the issue was explained from the standpoint of a specific player. Or the issue was explained in terms of one player versus another player. It was apparently far harder for students to find the issue faced by all the players, and phrase it independently of the actual players, e.g., as "Is it right or wrong to ...?" or "Is ... good or bad?"
In step 3, many students struggled to find more than one or two solutions to each ethical problem. It was evident these students pre-judged to the extent that they could identify only solutions acceptable to them. It was as if they had (horse) blinkers on, blinding them to other alternatives. Students had to be reminded to put aside their prejudices (until step 5) and to consider any half reasonable solution. When presented with a solution they had not thought of, many students seemed genuinely surprised it was worth considering. The point had to be made that the 'worth' of each solution is evaluated only in steps 4 and 5, not before.
In step 4, most students were initially perplexed. This was to be expected until students were introduced later in the course to some ethical theories, and their basis in one or more intrinsic (rather than instrumental) values. Nevertheless, it seemed hard for students to recognise that if a solution embodied telling the truth, for example, then the underlying value (or outcome) of that solution is honesty.
In step 5, most students had little trouble selecting their preferred solution. It was generally the first solution they thought of (indicating their personal bias). However, it was hard for many students to prioritise the solutions, based on their ranking of the underlying values. Knowledge of ethical theories later in the course allowed students to improve steps 4 and 5 immensely.
3 CRIME AND ETHICS INVESTIGATION
Observing the difficulties faced by our students when analysing an ethical issue (section 2.2), we looked for ways to help their strengths overcome these weaknesses. Most of our students are strong in mathematics and sciences. They are inclined to investigate technical issues in a systematic way. Crimes are investigated scientifically these days, and most of our students are familiar with 'whodunnit' novels, police shows, detective stories, thrillers and mystery books. Anecdotal evidence suggests the recent spate of forensic crime investigation television shows (CSI, Cold Case, Without a Trace, Law and Order: Special Victims Unit) appeal to a large majority of our multicultural students.
We decided to introduce our students to a standard investigative procedure used by policing authorities to solve crimes in general (section 3.1). Then, arguing by analogy, we adapt the crime investigation procedure to investigate ethical 'crimes' (issues). Our ethical crime investigation procedure is detailed in section 3.2. We evaluate its success in section 3.3 and in section 3.4 we address perceived limitations in the analogy.
3.1 Crime investigation procedure
The following investigative procedure extends a standard five-step procedure used by policing authorities to reconstruct crime scenes (Baldwin, 2000): interview, examine, photograph, sketch and process. These steps are compressed into steps 1 to 3 below. Our step 3 extends the 'process' step to begin theorising as to what transpired and who is responsible (O'Connor, 2004). Our five steps are also an abstraction of the comprehensive procedure in the United States Department of Justice (2000) guide, Crime Scene Investigation.
- recognise a crime may have occurred in a given situation
- secure the crime scene
- collect evidence
- identify the victim(s), suspects, witnesses and bystanders
- collect statements
- locate any party who departed the scene
- explain the facts of what happened
- formulate alternative hypotheses (theories)
- include motive and means for each possible perpetrator
- eliminate suspects and hypotheses
- charge most likely perpetrator(s)
We ask our students to apply the above procedure, actively or passively, while watching their favourite television crime show. The intention is to convince them that the procedure works, not only in television crime scripts but also for real criminal investigations.
Interestingly few students ask how to carry out the above steps. Apparently familiarity with crime fiction provides the relevant investigative skills! We seek to transfer this know-how to the investigation of ethical 'crimes'.
3.2 Ethical crime investigation procedure
We propose the following analogous investigative procedure to analyse an ethical issue:
- Recognise an ethical issue may exist in a given situation
- quarantine the situation while under investigation
- collect evidence, e.g., disputed normative claims
- Identify the participants, stakeholders and victims; i.e., identify the players or parties
- collect statements, documents, facts
- notify any relevant external parties
- Explain the ethical problem faced by the players; i.e., define the moral dilemma
- Formulate alternative solutions to the ethical problem; i.e., list the options
- clarify the principles, values and outcomes underlying each solution
- Prioritise the alternative solutions in terms of their values and outcomes; i.e., state your preferred solution to the ethical problem
- give a short rationale for your decision
- generalise where possible
We set our students an assignment to apply the above procedure to analyse three IT ethical issues, each encapsulated in one of Johnson's scenarios (Johnson, 2001).
3.3 Evaluating our ethical crime investigation procedure
In section 2.2 we reported the difficulties our students formerly encountered when using a basic procedure for analysing an ethical issue. We now ask students to use the refined procedure in section 3.2 – our ethical crime investigation procedure. We discuss the results of a preliminary summative evaluation below.
We compared the results for two student cohorts on the same assignment, which analyses three IT ethical issues (see section 2.2). The 2003 cohort was the last to use the basic procedure described in section 2.2. The 2004 cohort was the first to use our ethical crime investigation procedure, as described in section 3.2. Apart from the change of investigation procedure, no other variable was intentionally altered between the two cohorts; i.e., assignment specification, duration, marking scheme and percentage contribution to total grade remained the same.
Each cohort contained over 300 students. The average grade gained by the 2004 cohort was 12% higher than the 2003 cohort. The 2004 cohort showed no similar improvement in other assessable components of the course. We tentatively conclude that our ethical crime investigation procedure is beneficial. However, confirmation will require further evaluation. After interviewing a random sample of twenty 2004 students, we attribute the improvement to students adopting a crime solving mind-set that emphasises an open-minded attitude while using scientific rigour to mount and test hypotheses.
On average the 2004 cohort differentiated the players in step 2 better than the 2003 cohort did in their equivalent step 1. The facts collected in 2004 were also more complete, and included fewer irrelevancies than in 2003. Overall we felt the 2004 cohort was more clinically accurate. This was also evident in step 3, where the ethical issue was expressed more concisely and exactly. By comparison, the 2003 cohort had difficulty isolating the main issue (in their step 2) from the various players' perspectives on it. The 2004 cohort certainly formulated alternative solutions to the ethical issue more comprehensively.
Admittedly both cohorts still have difficulty clarifying the principle or value underlying each solution, and hence prioritising the alternatives. This requires at least the following skills, which are introduced later in our course:
- Ability to conduct a dialectic
- Ability to discriminate between descriptive and normative claims
- Ability to discriminate between instrumental and intrinsic values underlying normative claims and
- Ability to incorporate one or more ethical theories.
Revisiting the same assignment, the students are asked to use the above skills to expand each of the five steps in our ethical crime investigation procedure, but this is beyond the scope of this article.
3.4 Limitations of our ethical crime investigation procedure
We tell students there are limitations in the analogy between the investigation of crimes and ethical issues. The former is more concerned with descriptive claims (supported by evidence) and instrumental values (e.g., money). The latter is more concerned with normative claims (prescribing how people ought to act) and intrinsic values. Nevertheless we argue that normative claims are like the clues at a crime scene. Both can be found and analysed with a similar procedure (sections 3.1 and 3.2).
We tell students relatively little about how to carry out the steps in our ethical crime investigation procedure, relying on their knowledge of crime investigation procedure as a guide. We claim that answering how to recognise an ethical issue is similar to recognising a crime has occurred (step 1 in the analogous procedures). When neither the issue nor the crime is obvious, recognition comes from keen observation that detects some detail out of place, e.g., contradictory prescriptive statements.
It can be argued that crime investigation must be without fear or favour, whereas the investigation of an ethical issue must take the interests of stakeholders into account. We maintain that the respective stakes should be examined similarly to the motives and means of the suspects in a crime investigation. The cases made for and against should determine the outcome of an investigation, not the influence of any particular stakeholder or suspect.
We assert that the perceived limitations listed above in our analogy between the investigation of crimes and ethical issues are in fact strengths rather than weaknesses.
4 AN EXAMPLE OF CRIME AND ETHICS INVESTIGATION
As an exercise for students in applying our ethical crime investigation procedure (section 3.2), we scripted a scenario for video production (Zuluaga & McKay, 2004). The video depicts events surrounding a petty theft in a busy open plan office. We first investigate the crime (section 4.1) and then we similarly investigate underlying ethical issues (section 4.2). This video was not available during the evaluation of our ethical crime investigation procedure reported in section 3.3.
4.1 Crime investigation scenario
The video shows an employee, Sophie, at her office workstation starting her personal banking online, but she is called away. As the camera follows Sophie, the audience sees her colleagues, Holly, Sam and then Bill walk near her desk. Sophie returns to find $1,000 suddenly missing from her bank account.
The narrator then relates that Sophie reports the theft to her manager and describes what she saw. Holly, Sam and Bill immediately become suspects. Sophie's manager begins a preliminary investigation. Sophie's bank is asked to trace the transaction in question. Apparently Sophie's $1,000 was transferred to another account at the same bank, and has since been withdrawn, probably by an accomplice. This account is clearly under a false name and identity.
At intermission 1, the students are asked to start applying the crime investigation procedure in section 3.1, specifically steps 1, 2 and 3. The video resumes with Sophie's manager interviewing the suspects. The picture has four frames – one for each suspect and one for the manager who interviews them separately. As the narrator relates the interview with each suspect, the audience see that person's frame become active.
Sam says he was having a conversation with Holly. He claims he never saw Sophie leave her workstation and was not aware of anyone approaching it. After the conversation with Holly, he returned to his own workstation. He thinks Holly went back to hers but can't be absolutely sure. He has no idea when Sophie arrived back in the office, as he claims he never knew that she had left it in the first place.
Holly says she was talking to Sam. Like Sam, she claims she never saw Sophie leave her workstation or return to it. She did, however, notice Bill leaning over Sophie's desk.
Bill says he didn't see Sophie leave the room but did see Holly and Sam talking near Sophie's desk. He admits to looking around Sophie's workstation for a yellow sticker pad so he could note down a reminder to phone his wife. He produces the yellow sticker with his wife's number on it.
At intermission 2, the students complete step 4 of the crime investigation procedure and they are asked what they need in order to complete step 5. The video resumes with Sophie's manager making telephone calls to check up on each suspect. As the narrator relates what the manager learns about each suspect, that person's portrait appears on screen.
The audience learns that Holly was questioned about a previous theft two years before but no charges were laid, that Sam was a chronic latecomer to work and considered unreliable by a previous employer and that Bill was passed over for promotion three months ago and is known to be a heavy gambler.
Finally the students are asked to complete step 5 of the crime investigation procedure. All three suspects have circumstantial evidence against them, but a more thorough investigation will be needed if any incriminating proof is to be unearthed. Sophie's manager has to decide whether to call the police to conduct an official investigation, as there are reputations and jobs at stake, not to mention office morale.
4.2 Ethical crime investigation scenario
Next we ask the students if they recognise any ethical issues in the theft scenario and its investigation. To help them adapt to this new perspective, the three-part video is shown again. After each part, we prompt the students with questions such as the following.
Video 1 ethical issues:
Should Sophie do her personal banking online while at work? How responsible is Sophie for the ensuing theft? Is leaving her online banking account open like leaving her purse on the desk while she goes away? Or is her online account effectively pickpocketed while her attention is elsewhere? Does Sophie's degree of blame affect whether the theft should be investigated? Should Sophie's employer offer to repay her and let the matter drop? Or should the theft be investigated no matter what?
Video 2 ethical issues:
If investigation is warranted, who should conduct it – Sophie's manager, Sophie's bank or the police? Should Sophie's manager have authority to interrogate employees as witnesses and possible suspects? Or should Sophie's bank lead the investigation? If so, should the bank divulge what it finds out to Sophie's employer or only to Sophie? Or should the bank forward the result of their investigation only to the police and request them to investigate further? Should Sophie cooperate with the initial investigation by her manager (involving the bank) or should she simply report the theft to the police and expect them to conduct any further investigation?
Video 3 ethical issues:
Should Sophie's manager have authority to access employee records to check up on the suspects? Should any unearthed private information in employee records be divulged to Sophie, Sophie's bank or the police? Should Sophie, Sophie's employer, the bank or the police use any of the circumstantial evidence about the suspects against them?
In summary, we intend students to recognise at least the following ethical issue in each successive part of the video:
- Has a crime been committed that is worth investigating?
- Who should conduct any investigation(s)?
- Should private information in employee records be used as circumstantial evidence?
Our students are asked to focus on one of these ethical issues and apply our ethical crime investigation procedure (section 3.2). So far only anecdotal evidence is available to suggest the video assists students to analyse better an ethical issue. At the very least, the video seems appreciated for the extra practice it provides.
5 AN ETHICAL CRIME LEARNING OBJECT
We outline below our use of the object oriented learning methodology (OOL) (Morris, 2005) to design a class of LOs or learning object class (LOC). The resulting LOC, Investigator, and its 'children' are intended to help online students learn to investigate ethical issues, using our ethical crime investigation procedure (section 3.2) and example video (section 4).
Section 5.1 briefly explains the OOL methodology and how it benefits the design of LOCs. Section 5.2 explains how a student can interact with LOs that are dynamically created instances of class Investigator's children. Section 5.3 explains the reusability of class Investigator and its children in future lessons.
5.1 Object oriented learning methodology
OOL applies object oriented software engineering (Pleeger, 2001) to the design of LOs. A prospective LO's attributes and activities are first 'abstracted' into a LOC. Figure 1 below depicts class Investigator's attributes (e.g., problem, players) and activities (e.g., recognise, identify).
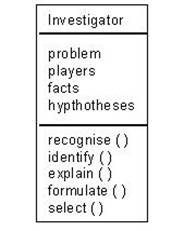
Figure 1: Class Investigator
Class Investigator recognises a problem to be investigated, identifies the involved players, explains the relevant facts, formulates at least two hypotheses and finally selects the best solution. Class Investigator is an abstract LOC that can be extended into other more concrete and useful LOCs as follows.
In Figure 2 below, we extend class Investigator into classes Crime Investigator and Ethic Investigator. Figure 2 uses the Unified Modelling Language (UML), a standard for diagrammatically depicting relationships between classes (Priestley, 1996).
Both 'child' classes inherit attributes and activities from their parent. These can be overridden (via polymorphism), specialised and aliased in the respective child classes. OOL facilitates the design of a hierarchy of LOCs. OOL thereby enhances the reusability of a LOC in future lessons.
Furthermore, OOL facilitates dynamic creation (instantiation) of an individualised LO for, or by, a student during an online lesson (see below).
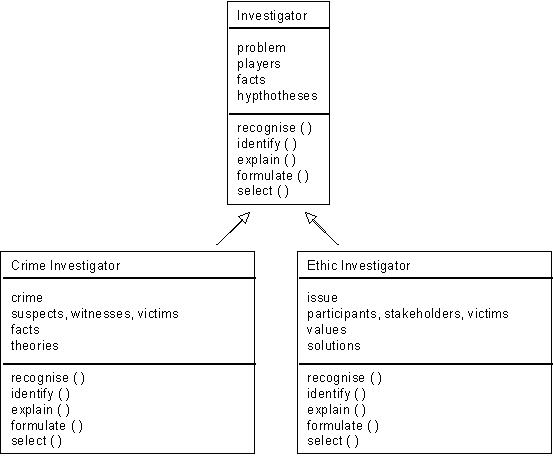
Figure 2: Class Investigator and its 'child' classes
5.2 Class Investigator online lessons
When class Crime Investigator is instantiated, the student can interact with video 1, 2 and 3, with guidance from the narrator's voice in between (section 4.2). The activities explain and illustrate the five steps in the crime investigation procedure (section 3.1).
When class Ethic Investigator is instantiated, the student can interact with video 1, etc. to solve an ethical issue nominated from the three listed in section 4.2. The student can instantiate a separate Ethic Investigator LO for each of the other issues. The student can interactively contribute to each step and check against prepared answers (partial or complete).
Teachers can reuse both these classes by 'plugging in' new crimes and ethical issues, as explained in section 5.3. Each LOC can be integrated into a new lesson by meeting the specifications of a Java-like interface type that defines the 'look and feel' of the new lesson (Morris, 2005).
5.3 Class Investigator reusability
In a software system, coupling measures how cleanly class objects are partitioned. Cohesion measures how closely activities in an object are related. Coupling and cohesion are interdependent measures – the less cohesive an object, the more likely it is coupled with other objects. The more coupled an object is with other objects, the harder it is to alter or upgrade the class object in isolation, which lowers maintainability. A strongly coupled class object is less reusable without significant maintenance (Morris, 2005).
Class Investigator is sequentially cohesive (Yourdon & Constantine, 1978) because the output of each activity is input to the next activity: identifying the relevant players requires recognition of the problem; explaining the facts requires identification of all players; formulating plausible hypotheses requires all the facts; selecting a solution requires alternative hypotheses. Sequential cohesion is the second highest level and significantly strengthens reusability. The children of class Investigator inherit this strength.
6 CONCLUSION
This work provides a student centred platform for teaching and learning the investigation of ethical issues, both online and face-to-face. Our adaptation of a standard crime investigation procedure to the analysis of ethical 'crimes' appeals to students familiar with the current television crime investigation genre. And students less exposed to television, e.g., in remote regions, are often still familiar with 'whodunnit' novels, detective stories, crime thrillers and mystery books.
Evaluation of students using our ethical crime investigation procedure shows a 12% improvement in their grades (see section 3.3), which we attribute to a better appreciation of the need for rigour when analysing an ethical issue.
Our development of a video, which encourages students to investigate a petty crime and its underlying ethical issues, emphasises similarities in the respective investigations. The video can also be embedded in a LO for delivery online or via CD-ROM or television broadcast. These media will be utilised when the course is delivered 75% online in Africa and 50% online in Vietnam, Singapore and Malaysia.
To assist further online students learning to investigate ethical issues, we used the OOL methodology to design a class of LOs (see section 5). Class Investigator uses our ethical crime investigation procedure and example video. It facilitates extension by local staff and its offspring are reusable. Each 'child' facilitates dynamic instantiation of an individualised LO for, or by, a student during a lesson. This enables an online lesson to be not only more highly interactive but also far less predetermined in its sequence of activities for each student.
Thus we leverage information communication technologies to distribute our ethical crime investigation procedure, to students in both developing and developed countries. Local staff with limited experience should be able to facilitate student use of our relatively self-contained resources, as they encourage student self-directed learning. And staff with experience of the resources should be able to customise them.
We believe that further exploration into similarities between the investigation of crimes and ethical issues can lead to more precise techniques to investigate ethical issues. Also deserving further research are the theoretical, pedagogical and philosophical underpinnings of our overall approach. Finally, we intend to exploit the modularity and reusability of class Investigator by developing another example video, hopefully on a larger scale, to demonstrate that our overall approach is scalable to real world ethical issues.
ACKNOWLEDGEMENTS
Iain (John) McKay, Multimedia Producer, Educational Media Group, RMIT University
REFERENCES
Association for Computing (2005), "Computing Curricula 2005" (draft), http://campus.acm.org/public/comments/Draft_5-23-05.pdf Accessed 1 Aug 2005.
Baldwin, H.B. (2000), "Crime Scene Processing Protocol", http://www.feinc.net/cs-proc.htm Accessed 1 Aug 2005.
Johnson, D.G. (2001), Computer Ethics. Prentice Hall, 3rd Edition, ISBN : 0-13-083699-0.
Kalliman, E., & Grillo, J. (1996), Ethical Decision Making and Information Technology. McGraw Hill, 2nd Edition, ISBN : 0-07-034090-0.
Morris, E. (1999), "A Cyberspace Ethics Methodology". Australian Computer Journal. 31(3), pp. 83-88, ISSN 004-8917.
Morris, E. (2005), "Object Oriented Learning Objects". Australian Journal of Educational Technology. 21(1), pp. 40-59. http://www.ascilite.org.au/ajet/ajet21/morris.html Accessed 1 Aug 2005.
Morris, E., Zuluaga, R., Zuluaga, C. (2004), "Professional Computing Ethics, Law and Marketing", (COSC1146/1147) Lecture Notes, RMIT.
O'Connor, T. (2004), "Crime Scene Analysis", http://faculty.ncwc.edu/toconnor/315/315lect04.htm Accessed 1 Oct 2004.
Pfleeger, S.L. (2001), Software Engineering Theory and Practice. Prentice Hall, 2nd Ed., ISBN 0-13-093129-2.
Priestley, M. (1996), Practical Object-Oriented Design with UML, McGraw Hill, ISBN 0-07-118371-X.
United States Department of Justice (2000), "Crime Scene Investigation" http://www.fbi.gov/programs/lab/fsc/backissu/april2000/twgcsi.pdf Accessed 1 Aug 2005.
Yourdon, E., Constantine, L. (1978), Structured Design: Fundamentals of a Discipline of Computer Program and Systems Design, Prentice Hall. ISBN 0138544719.
Zuluaga, C., & McKay, J. (2004), "Script for I.T. Crime / Ethics Investigation" http://goanna.cs.rmit.edu.au/~ted/Script for Ethics Discuss.doc Accessed 1 Aug 2005.
Copyright for articles published in this journal is retained by the authors, with first publication rights granted to the journal. By virtue of their appearance in this open access journal, articles are free to use, with proper attribution, in educational and other non-commercial settings.
Original article at: http://ijedict.dec.uwi.edu//viewarticle.php?id=116&layout=html
|